OpenShift console install
The instructions below are for installation via OpenShift console, as an option you can use Kubectl command line installation.
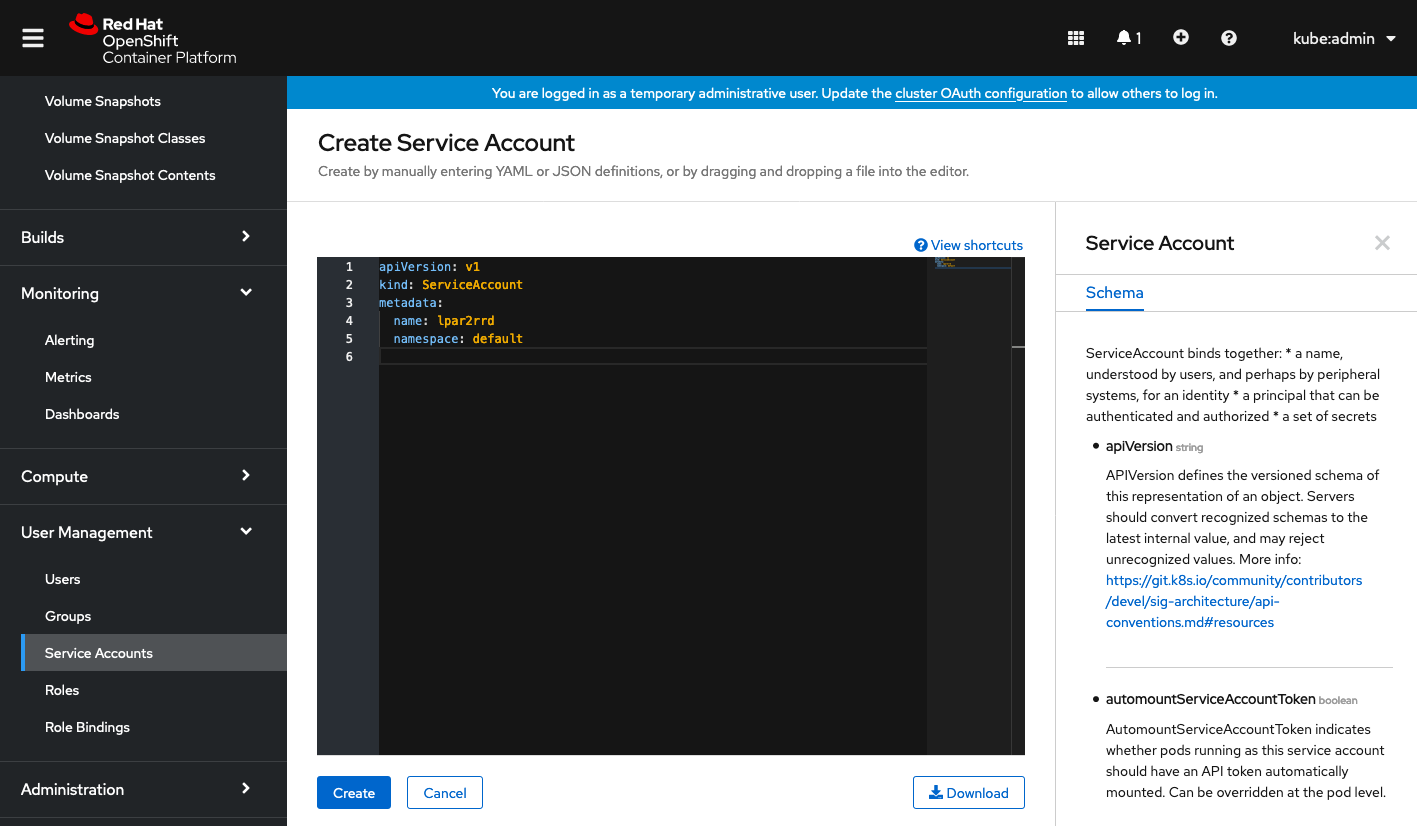
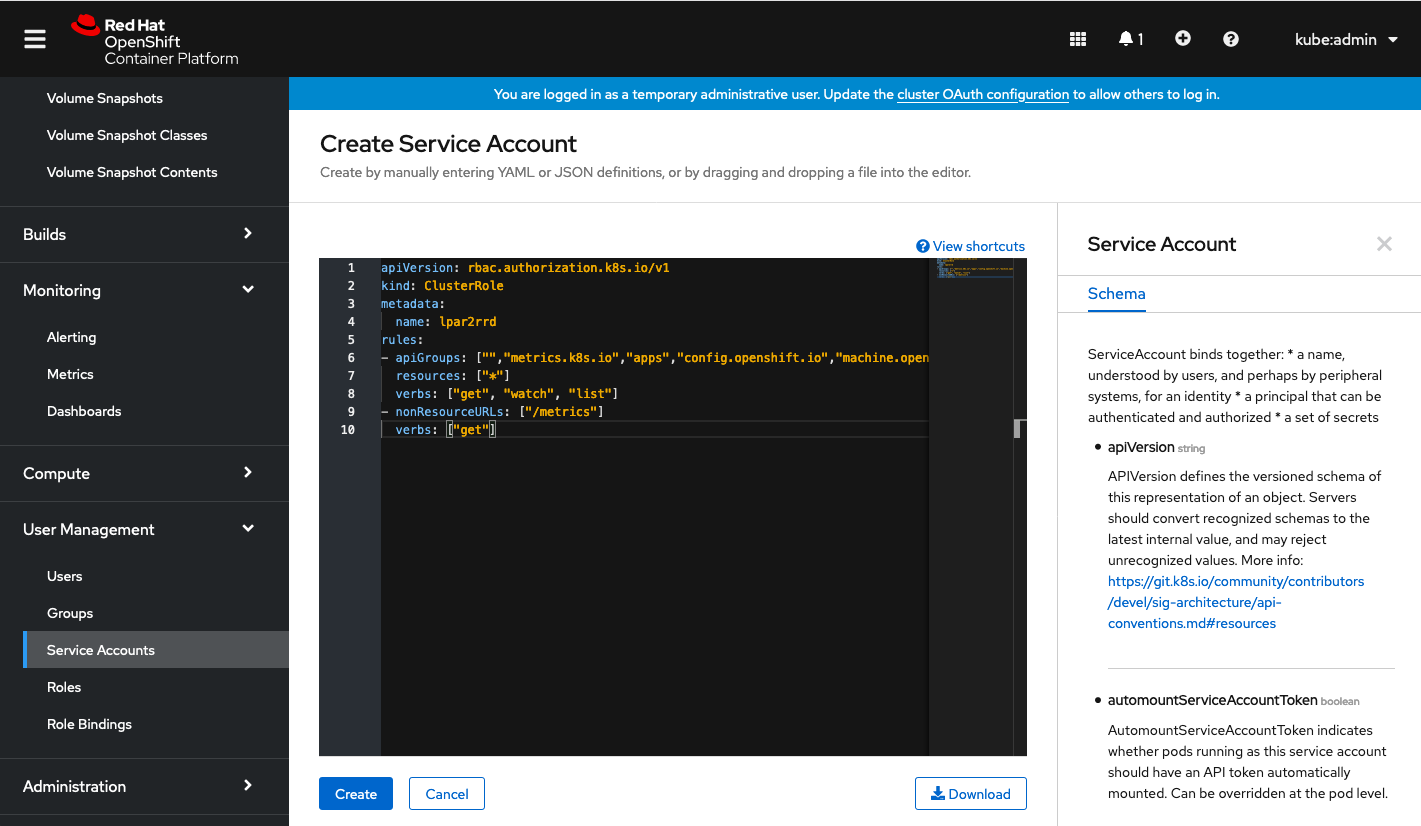
Create a xormon service account
You can choice whatever else account name than xormon.
Insert content below:
apiVersion: v1
kind: ServiceAccount
metadata:
name: xormon
namespace: default
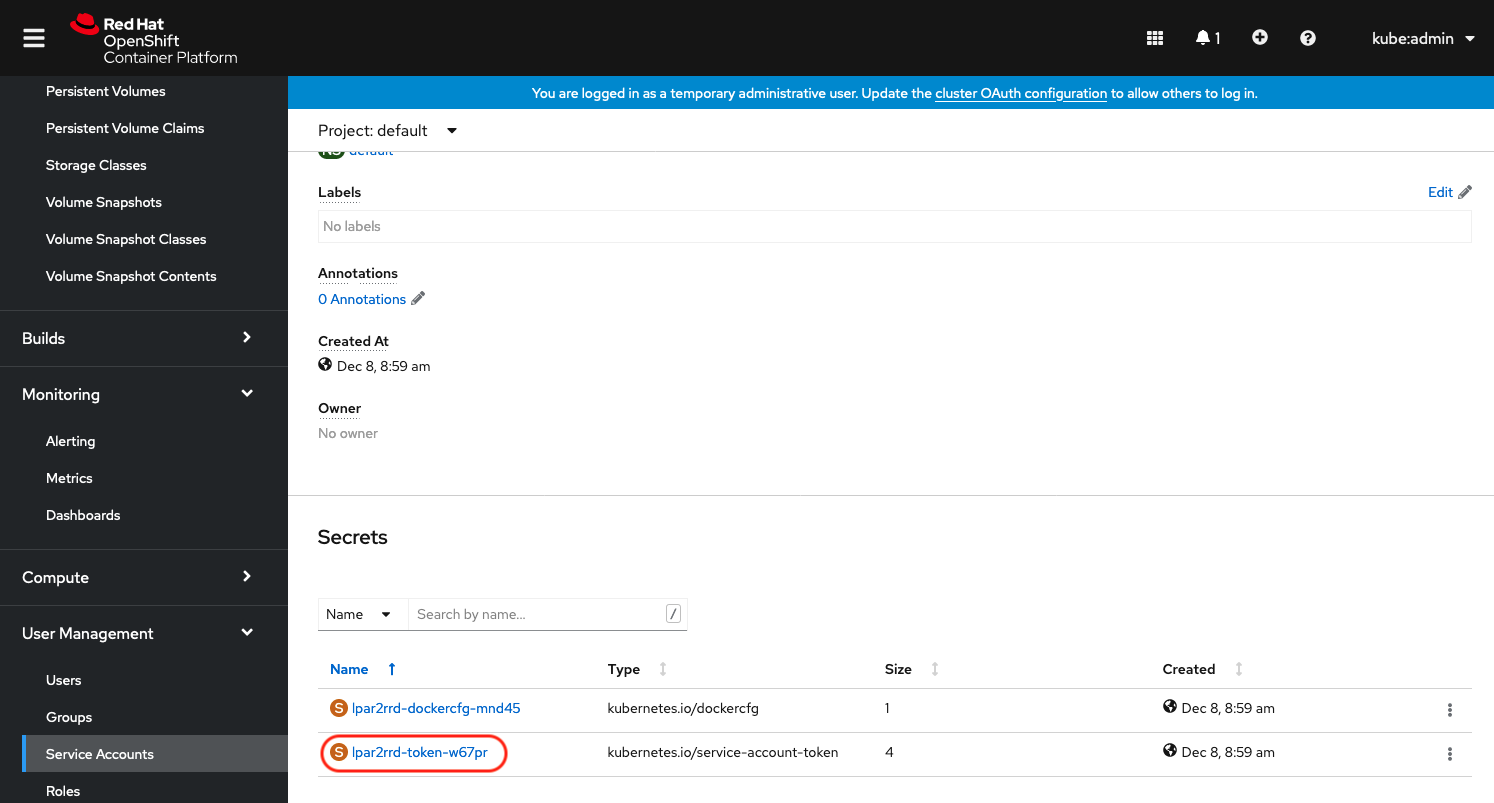
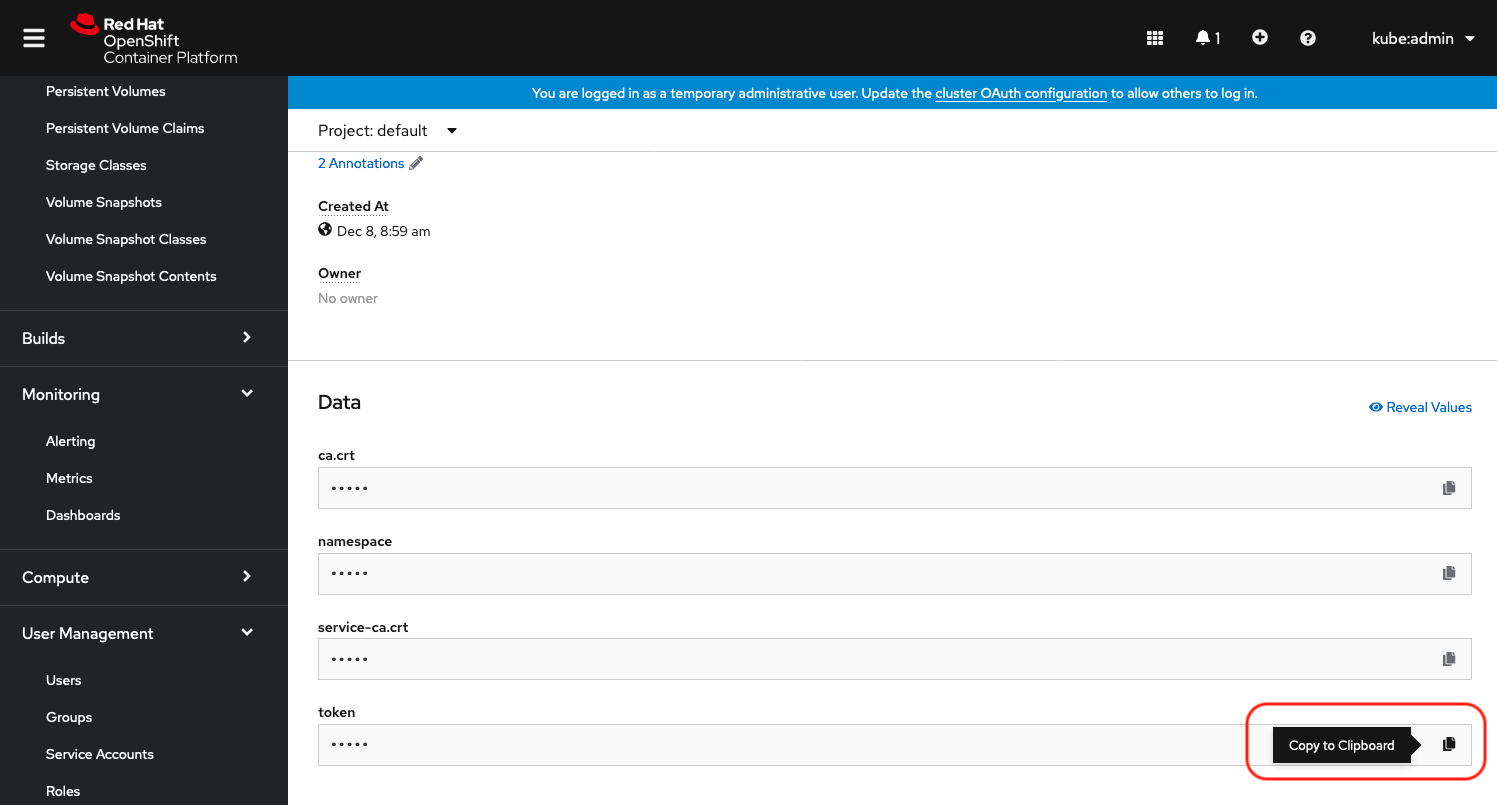
Click on "xormon-token-xxxxx" under to "Secrets"
Copy xormon token
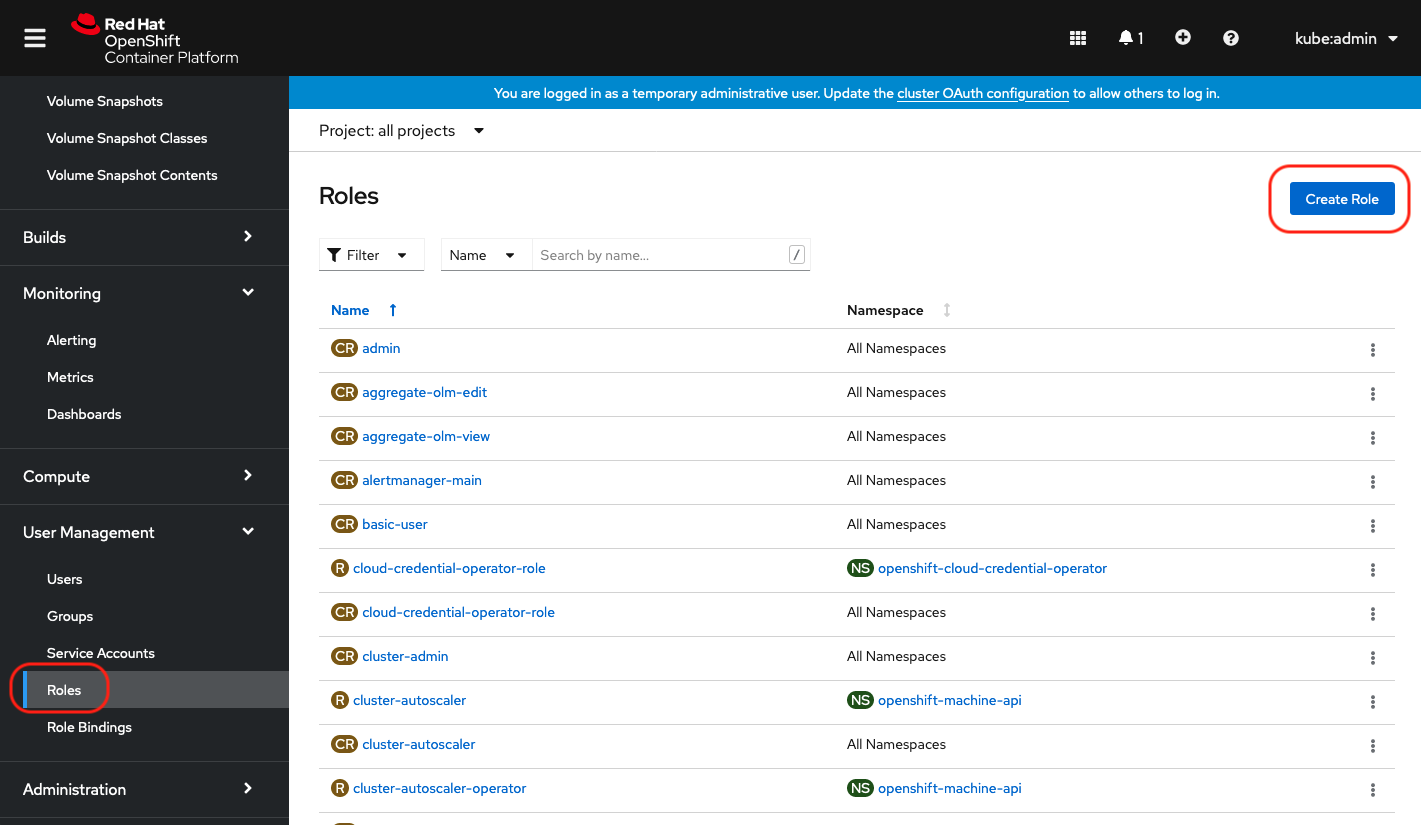
Create a xormon role
Insert content below:
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
name: xormon
rules:
- apiGroups: ["","metrics.k8s.io","apps","config.openshift.io","machine.openshift.io","machineconfiguration.openshift.io","monitoring.coreos.com","project.openshift.io","route.openshift.io","storage.k8s.io"]
resources: ["*"]
verbs: ["get", "watch", "list"]
- nonResourceURLs: ["/metrics"]
verbs: ["get"]
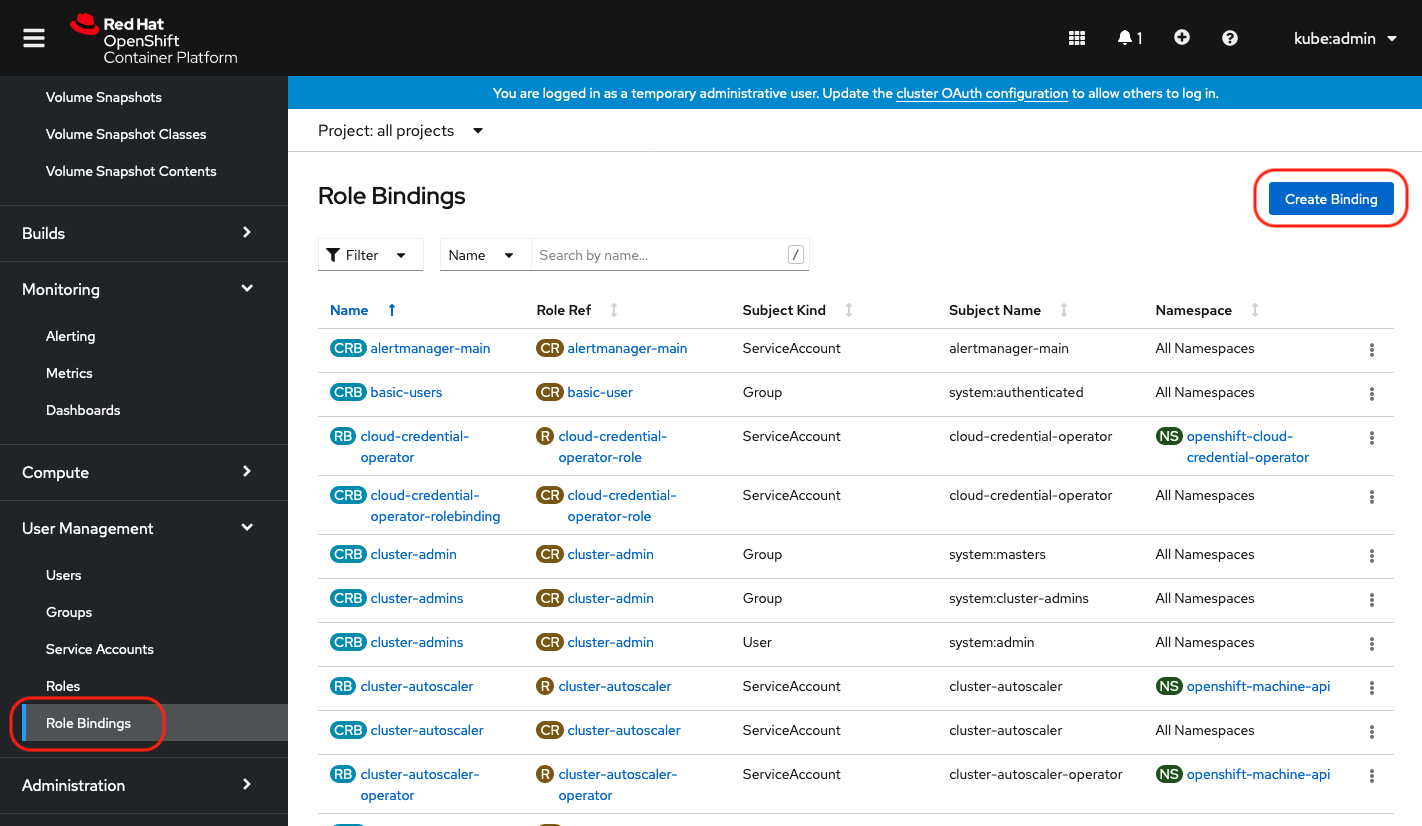
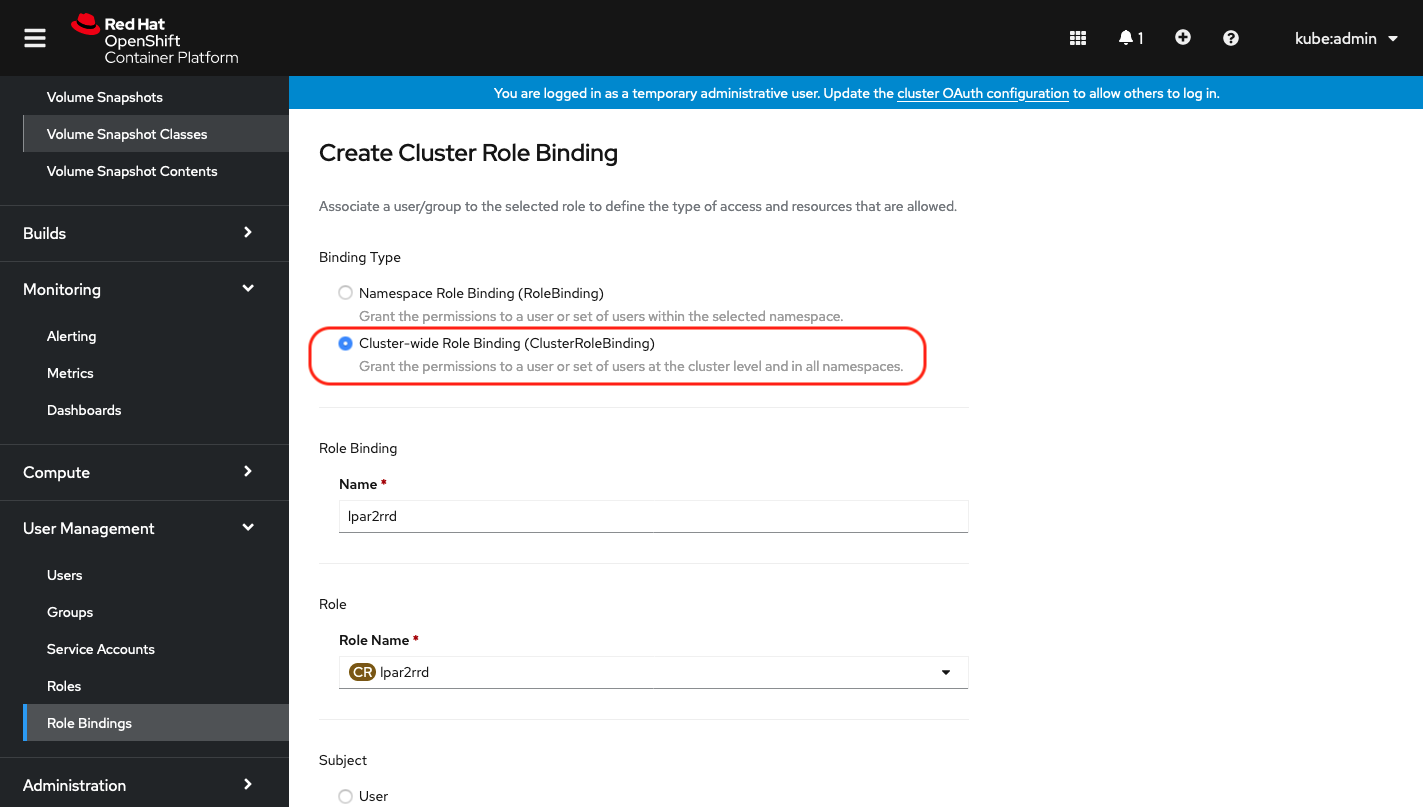
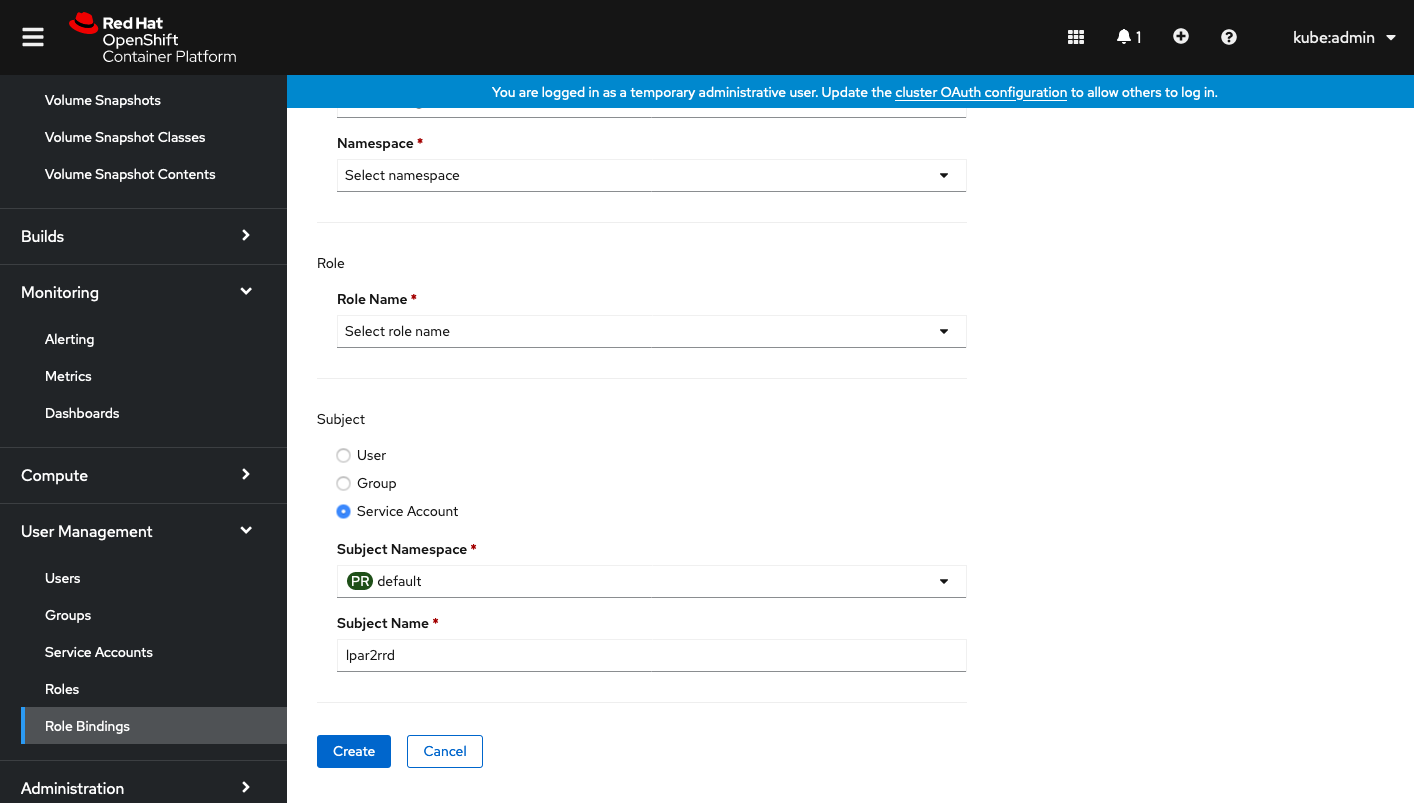
Create a xormon role binding
Select Binding type "Cluster-wide Role Binding", type the role binding name to "xormon" and select Role Name "xormon"
Select Subject "Service Account" and type "xormon" as Subject Name
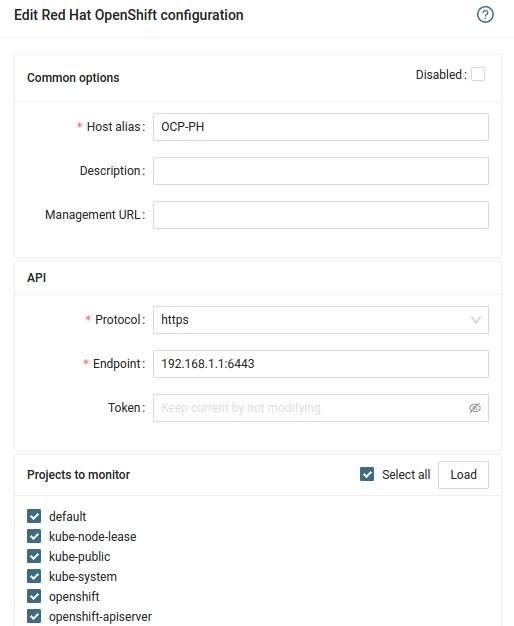
Configure RedHat OpenShift in XorMon NG
-
Open network connection to the RedHat OpenShift from XorMon NG server.
If it is in Google Cloud then port 443, if it is in Kubernetes then port 6443.
-
XorMon NG UI ➡ Device ➡ Conteiner ➡RedHat OpenShift ➡ New
- Run "Test" for configured OpenShift host, it must show "OK"
-
Wait about 1 hour, then refresh the web browser cache by Ctrl-F5
Kubectl install
The instructions below are for installation via the
kubectl command line as an option to OpenShift console installation
Create a xormon service account
You can choice whatever else account name than xormon.
$ kubectl create serviceaccount xormon
Create a clusterrole
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
name: xormon
rules:
- apiGroups: ["","metrics.k8s.io","apps","config.openshift.io","machine.openshift.io","machineconfiguration.openshift.io","monitoring.coreos.com","project.openshift.io","route.openshift.io","storage.k8s.io"]
resources: ["*"]
verbs: ["get", "watch", "list"]
- nonResourceURLs: ["/metrics"]
verbs: ["get"]
Apply it by:
$ kubectl apply -f ClusterRole.yml
Create a clusterrolebinding
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: xormon
subjects:
- kind: ServiceAccount
name: xormon
namespace: default
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: xormon
Apply it by:
$ kubectl apply -f ClusterRoleBinding.yml
Get xormon token
$ kubectl get serviceaccounts xormon -o yaml
$ kubectl describe secret xormon-token-fkkxp
Get cluster endpoint
$ kubectl config view
Configure RedHat OpenShift in XorMon NG
-
XorMon NG UI ➡ Device ➡ Conteiner ➡RedHat OpenShift ➡ New
- Run "Test" for configured OpenShift host, it must show "OK"
-
Wait about 1 hour, then refresh the web browser cache by Ctrl-F5
Docker monitoring is performed via the OS agent in a container. Deploy the agent on each monitored Docker host.
Prerequisites
- Opened TCP communication between each Docker server and XorMon NG server on port 8162.
Connections are initiated from Docker server side.
Docker agent installation
- Pull the image
# docker pull xorux/lpar2rrd-docker-agent
- Run the docker agent
# docker run -d --hostname $(hostname) --name lpar2rrd-docker-agent -v /var/run/docker.sock:/var/run/docker.sock:ro --env XORMON=<XorMon-NG_hostname/IP> xorux/lpar2rrd-docker-agent
XorMon NG
-
Wait about 1 hour, then refresh the web browser cache by Ctrl-F5
Data is obtained from Kubernetes API & Kubernetes Metrics server API
Check if you have metrics-server installed
kubectl get pods -n kube-system
Create a xormon serviceaccount
$ kubectl create serviceaccount xormon
Create a clusterrole
Create file ClusterRole.yml with this content:
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
name: xormon
rules:
- apiGroups: ["","metrics.k8s.io"]
resources: ["pods","nodes","services","nodes/proxy", "endpoints", "namespaces"]
verbs: ["get", "watch", "list"]
- nonResourceURLs: ["/metrics"]
verbs: ["get"]
Apply it by:
$ kubectl apply -f ClusterRole.yml
Create a clusterrolebinding
Create file ClusterRoleBinding.yml with this content:
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: xormon
subjects:
- kind: ServiceAccount
name: xormon
namespace: default
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: xormon
Make sure it is the same namespace as the serviceaccount like
default above.
Apply it by:
$ kubectl apply -f ClusterRoleBinding.yml
Get xormon token
Create file Lpar2rrdSecret.yml with this content:
apiVersion: v1
kind: Secret
metadata:
name: xormon-token
annotations:
kubernetes.io/service-account.name: xormon
type: kubernetes.io/service-account-token
Apply it by:
$ kubectl apply -f Lpar2rrdSecret.yml
Get xormon token:
$ kubectl describe secret xormon-token
Get cluster endpoint
$ kubectl config view
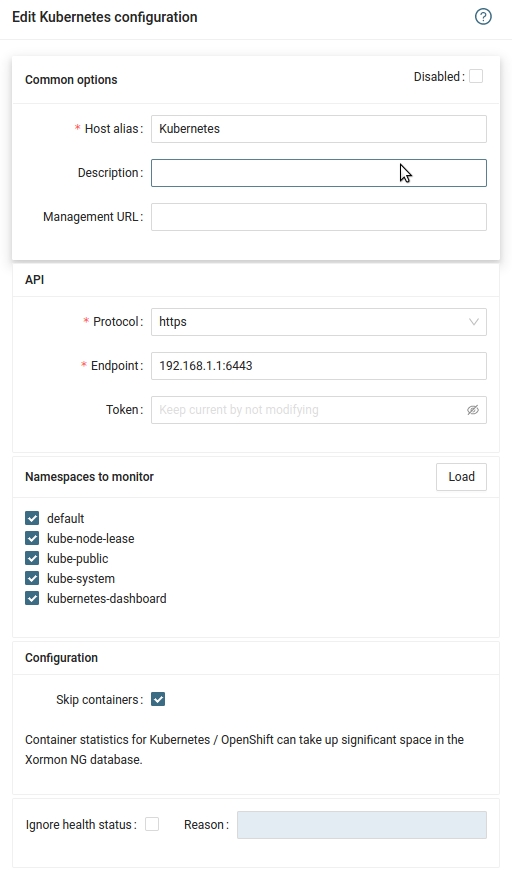
Configure Kubernetes in XorMon NG
-
XorMon NG UI ➡ Device ➡ Container ➡ Kubernetes ➡ New
- Run "Test" for configured Kubernetes host, it must show "OK"
-
Wait about 1 hour, then refresh the web browser cache by Ctrl-F5